When it comes to disaster recovery planning, two important metrics to consider are RTO (Recovery Time Objective) and RPO (Recovery Point Objective). Both RTO and RPO play a critical role in disaster recovery, ensuring businesses can effectively recover data and minimize company downtime. There are many aspects to consider when developing a disaster recovery plan as the process is a balance of technical resources, company needs, and money. Backup plans with minimal downtime and minimal data loss can be expensive and that is why it is vital to work with an experienced managed service provider to create a disaster recovery plan and a business continuity plan.
What is RTO?
We often hear people saying, “RTO vs RPO”, but this is a misunderstanding. These are two separate factors to consider when discussing disaster recovery. Simplified: RTO is downtime. RPO is data loss.
RTO (Recovery Time Objective) is a metric that defines the maximum amount of time it should take for a business to recover and resume normal operations after a disaster. It is the time frame that systems, applications, and data should be fully functional again. RTO is typically measured in hours or days and is a critical factor in deciding the level of downtime a business can tolerate. The shorter the RTO, the faster a business can recover from a disaster and minimize the impact on operations.
What is RPO?
RPO (Recovery Point Objective) is a metric that defines the maximum amount of data loss a business can tolerate. It is the interval between when systems, applications, and data run a backup. RPO is commonly measured in hours and is crucial in figuring out frequency of data backups and the level of data protection a business needs. The shorter the RPO, the less data a business will lose in the event of a disaster.
Most clients are comfortable with an hour recovery point, but some clients may need a recovery point involving minutes. Meaning most clients are okay with possibly losing up to an hour’s worth of work for their company. For example, an employee updates a chart weekly. In this scenario, an individual updates it at 9:45am and the server crashes at 9:58am. Data can be recovered as far back as 9am that morning. Any work done after 9am would have to be recreated.
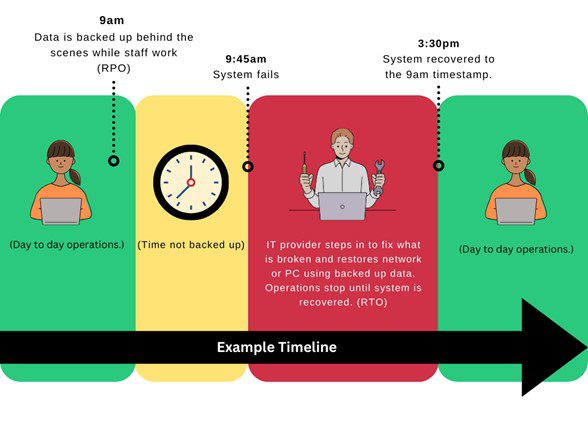
Disaster Recovery Plan: Figuring out RTO and RPO Allowances
When creating a Disaster Recovery Plan, critical software, applications, and data must be considered when planning for RTO and RPO. One of the first steps to a disaster recovery plan is to show what is essential for a business operation and prioritize their recovery. Consider a separate server for critical systems. In a disaster, these applications must be restored quickly, keeping data separate will allow for a faster recovery or restore time. For example, if the server is running a financial application such as QuickBooks and you need that software to run payroll. How quickly does data need restored so employees can be paid? Other applications that may need to be restored quickly include CAD, CNC, medical technologies, and critical line of business applications. Large storage drives take longer to restore. If you are hosting applications on servers with a single large drive, you could be without that application for days.
Alternately, documents needing to be archived or don’t need to be regularly updated, can be backed up once a week while other documents and tools may need to be backed up once a day or every hour. It is the IT provider’s responsibility to work with the business to create an effective backup policy that meets their needs.
Companies need to evaluate the potential impact of downtime on their business by considering factors such as financial losses, customer dissatisfaction, and reputational damage. This will help decide acceptable levels of downtime and recovery time for your organization. Additionally, it’s important to assess the IT provider and their resources. Determine necessary technology, personnel, and processes in place to achieve the desired RTO and RPO. Lastly, it is important to consider any regulatory or compliance requirements that may affect disaster recovery planning. Ensure RTO and RPO align with these obligations to avoid any legal or financial consequences. By considering these factors, a proper RTO and RPO can be decided for your business.
Strategies for Achieving RTO and RPO
There are several strategies to be implemented to achieve desired RTO and RPO goals in disaster recovery planning.
- Prioritize systems: Identify critical systems, applications, and data essential for business operations. Focus on recovering these first to minimize downtime and ensure business continuity.
- Implement redundant systems: Consider implementing redundant systems or backup solutions to reduce risk of data loss and minimize recovery time. This can include using backup servers, cloud storage, or off-site data centers.
- Regularly test disaster recovery plan: Regularly test disaster recovery plan to ensure its effectiveness and identify any potential gaps or weaknesses. This can involve conducting simulated disaster scenarios evaluating an organization’s response and recovery capabilities.
- Invest in reliable technology: Ensure IT infrastructure is equipped with reliable and up-to-date technology. This includes hardware, software, and network infrastructure that can support quick data recovery and minimize downtime.
- Train staff: Provide training and education to staff on disaster recovery procedures and protocols. This will help staff have confidence and be prepared during a real crisis and can minimize the time it takes for the recovery process.
- Monitor and update the plan: Continuously monitor and update the disaster recovery plan to reflect any changes in business operations, technology, or regulatory requirements. Regularly review and revise RTO and RPO goals to align with evolving business needs.
- Consider outsourcing: If your organization lacks resources or expertise to effectively manage and implement a disaster recovery plan, consider outsourcing to a reputable disaster recovery service provider. They can help ensure RTO and RPO goals are met while providing expert support and guidance.
Achieving desired RTO and RPO levels can minimize the impact of a disaster on your business. Peace of mind about company data is achieved when there is a qualified, experienced MSP (Managed Service Provider) looking for you. At 4BIS Cyber Security, we have thirty years of experience. We love knowing we are keeping our client’s data secure and their employees working!
Contact us to discuss what data strategies would work best for your company.

