Email Security for Businesses: Essential Strategies to Reduce Cyber Threats
Email Security: 11 Ideas to Help Secure My Business Email Safeguarding email communication is vital for every business. Cybercriminals are increasingly sophisticated, and email remains…
Business Email Compromise: What your users need to know
Understanding Business Email Compromise (BEC): How to Spot It and What to Do Business Email Compromise (BEC) is one of the most dangerous threats to…
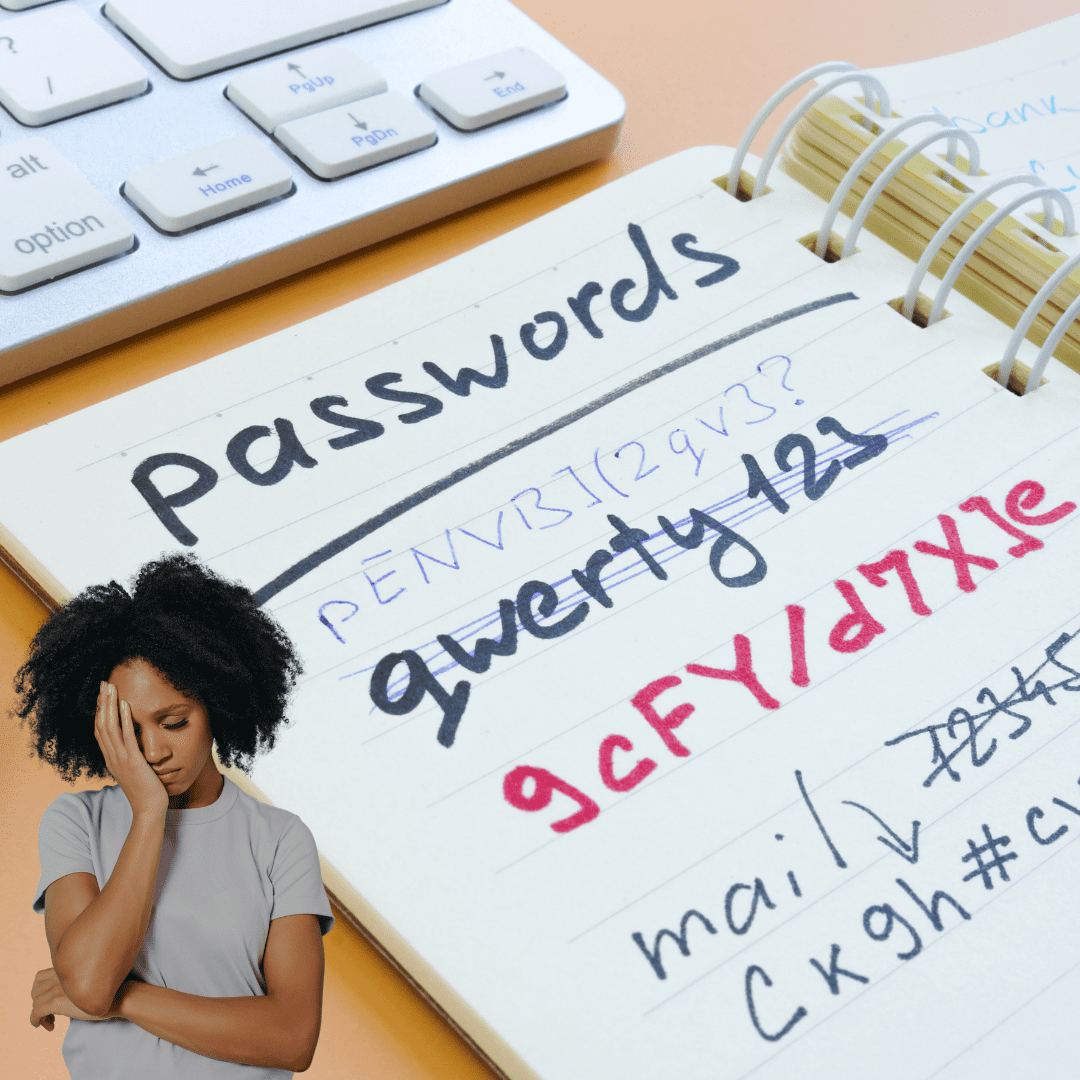
Password Security: A Cyber Security First Approach
The Importance of Password Security: A Cybersecurity First Approach In today’s digital landscape, passwords are the keys that unlock nearly everything we do online. Whether…
A New Era of Secure Remote Access: How SASE Outshines VPNs
SASE: How New Technology Can Help Secure Cincinnati Companies Cyber threats are always evolving. While you are working on your business, hackers are working on…
Passphrase vs Complicated Passwords – Passphrases Are Best
In the world of cybersecurity, the debate around password strength has seen significant evolution in recent years. Traditionally, experts advised creating complex passwords with a…
Personal Data Protection: Tips for Businesses and Consumers
We live in a technology dependent world where we are privileged to have instant communication and access to information readily available. However, these accessibility and…
Four Ways IT Helpdesk Services Can Enhance Your Daily Operations
Technology is essential to modern daily business operations. However, the complexity of IT systems isn’t always the easiest to understand. Software glitches and hardware malfunctions…
A Quick Guide to The Dos and Don’ts of Seeking IT Help
Software glitches, hardware malfunctions, and other technical issues are inevitable aspects of business operations. Organizations seek to invest in information technology helpdesks to manage them….
4BIS Featured in News About Cybersecurity Education Program
The Seven Hills School in Cincinnati, Ohio is launching a cybersecurity education program. This program is designed to get high school students interested in pursuing…
Understanding the Importance of Regular IT Audits
Businesses conduct assessments to see what strategies work and what requires tweaking for better performance. One of these assessments is an IT audit—a periodic check-up…